Overview
Note: This information is provided for archival purposes. Current documentation can be found in the Ksplice Enhanced Client User's Guide.
The Uptrack suite provide tools for managing Ksplice updates on your systems. To support various environments, Ksplice provides command line tools and a graphical interface.
Command Line Tools
uptrack-upgrade
Ksplice updates are the same security and bug-fix updates you would get from your Linux vendor,
packaged in a special reboot-less form.
To apply Ksplice updates, just run uptrack-upgrade:
# uptrack-upgrade -y The following steps will be taken: Install [guclwyc2] CVE-2012-0957: Information leak in uname syscall. Install [j4d07e02] Kernel panic in IPv4 ARP and IPv6 Neighbor Discovery. Install [r8og1ec4] CVE-2013-1979: Privilege escalation with UNIX socket credentials. Install [fiq04xbb] CVE-2013-2237: Information leak on IPSec key socket. Install [9q4luou3] CVE-2014-3687: Remote denial-of-service in SCTP stack. Installing [guclwyc2] CVE-2012-0957: Information leak in uname syscall. Installing [j4d07e02] Kernel panic in IPv4 ARP and IPv6 Neighbor Discovery. Installing [r8og1ec4] CVE-2013-1979: Privilege escalation with UNIX socket credentials. Installing [fiq04xbb] CVE-2013-2237: Information leak on IPSec key socket. Installing [9q4luou3] CVE-2014-3687: Remote denial-of-service in SCTP stack. Your kernel is fully up to date. Effective kernel version is 2.6.39-400.215.13.el6uek #
You can apply all available updates, bringing your system instantly up to date,
by running uptrack-upgrade -y,
or you can apply updates individually by specifying a Ksplice ID:
# uptrack-install guclwyc2 -y The following steps will be taken: Install [guclwyc2] CVE-2012-0957: Information leak in uname syscall. Installing [guclwyc2] CVE-2012-0957: Information leak in uname syscall. Your kernel is fully up to date. #
uptrack-show
You can see what updates have been installed by running uptrack-show:
# uptrack-show Installed updates: [guclwyc2] CVE-2012-0957: Information leak in uname syscall. [j4d07e02] Kernel panic in IPv4 ARP and IPv6 Neighbor Discovery. [r8og1ec4] CVE-2013-1979: Privilege escalation with UNIX socket credentials. #
You can see what updates are available to be installed
by running uptrack-show --available:
# uptrack-show --available Available updates: [fiq04xbb] CVE-2013-2237: Information leak on IPSec key socket. [9q4luou3] CVE-2014-3687: Remote denial-of-service in SCTP stack. #
uptrack-remove
Removing Ksplice updates is easy: just run uptrack-remove.
As with uptrack-upgrade, you can uninstall all updates,
bringing you back to your original stock kernel,
or uninstall individual updates by specifying a Ksplice ID:
# uptrack-remove -y The following steps will be taken: Remove [guclwyc2] CVE-2012-0957: Information leak in uname syscall. Remove [j4d07e02] Kernel panic in IPv4 ARP and IPv6 Neighbor Discovery. Remove [r8og1ec4] CVE-2013-1979: Privilege escalation with UNIX socket credentials. Remove [fiq04xbb] CVE-2013-2237: Information leak on IPSec key socket. Remove [9q4luou3] CVE-2014-3687: Remote denial-of-service in SCTP stack. # # uptrack-show Installed updates: None #
uptrack-uname
Ksplice Uptrack does not change the output of uname,
and uname will continue to reflect the version of the kernel
into which a machine was booted.
Instead, once you install updates,
use uptrack-uname to see what effective kernel a machine is running.
uptrack-uname has the same format as uname and supports the common uname flags,
including -r and -a.
Before installing updates, the original kernel and effective kernel are the same, and uname and uptrack-uname report the same information:
# uptrack-show Installed updates: None # uname -r 2.6.39-300.26.1.el6uek.x86_64 # uptrack-uname -r 2.6.39-300.26.1.el6uek.x86_64
After installing updates, uptrack-uname reflects the updated running kernel:
# uptrack-upgrade -y The following steps will be taken: Install [guclwyc2] CVE-2012-0957: Information leak in uname syscall. Install [j4d07e02] Kernel panic in IPv4 ARP and IPv6 Neighbor Discovery. ... Installing [fiq04xbb] CVE-2013-2237: Information leak on IPSec key socket. Installing [9q4luou3] CVE-2014-3687: Remote denial-of-service in SCTP stack. Your kernel is fully up to date. Effective kernel version is 2.6.39-400.215.13.el6uek # uname -r 2.6.39-300.26.1.el6uek.x86_64 # uptrack-uname -r 2.6.39-400.215.13.el6uek.x86_64
You can also see a machine's effective kernel on your web interface or through our API.
Configuration
Automatic updates
You can configure your systems to automatically install updates
as they become available.
To enable autoinstall, set autoinstall = yes in /etc/uptrack/uptrack.conf,
or pass the --autoinstall flag during installation.
# cat /etc/uptrack/uptrack.conf ... [Settings] ... # Uptrack runs in a cron job every few hours to check for and download # new updates. You can can configure this cron job to automatically # install new updates as they become available. # # Enable this option to make the cron job automatically install new # updates. # ... autoinstall = yes #
Autoinstall is our most popular configuration. It is a scalable way to ensure that updates get installed quickly as they become available, regardless of when they are released.
Enabling autoinstall does not mean the Uptrack client itself is automatically upgraded.
You will be notified via e-mail when a new Uptrack client is available, and it can be upgraded through your package manager.
Ksplice and Kernel Versions
Ksplice Uptrack updates your running kernel in memory. We recommended that, in addition to using Ksplice, you continue to use your package manager to update the kernel on disk as new kernels become available. That way, if a reboot becomes necessary (e.g. power loss or a hardware upgrade) you have the option of booting into a newer kernel. Under this plan, you would install all the updates available via both Ksplice Uptrack and your package manager.
Ksplice Uptrack also works great in environments where it is desirable to stay with a particular original kernel version (e.g. because of third party modules that are compiled against that kernel) but you want to stay up to date with all the important security and reliability updates for your kernel.
By default, Ksplice Uptrack will reinstall rebootless updates during the boot process
so you remain secure even after a reboot.
You can configure this behavior by changing the
install_on_reboot option in /etc/uptrack/uptrack.conf.
For example, to disable re-installing updates after a reboot:
# cat /etc/uptrack/uptrack.conf ... [Settings] # Automatically install updates at boot time. If this is set, on # reboot into the same kernel, Uptrack will re-install the same set of # updates that were present before the reboot. install_on_reboot = no ... #
install_on_reboot will restore the Linux kernel
to the same version as before rebooting.
There may be additional updates that could be applied.
If you wish all available updates for a particular kernel version to be applied,
set upgrade_on_reboot to yes.
# cat /etc/uptrack/uptrack.conf ... [Settings] ... # Automatically install all available updates at boot time, even if # rebooted into a different kernel. upgrade_on_reboot = yes ... #
Firewall and Proxy Configuration
The Uptrack client communicates with the Uptrack server
by connecting to https://updates.ksplice.com:443.
You can either make your firewall allow those connections,
or configure the Uptrack client to use a proxy server.
For information on hosting Ksplice updates on your own Yum repository, read about the Ksplice Offline Client. The Offline Client can be used to provide updates for machines not connected directly to the Internet.
To configure Ksplice Uptrack to use a proxy server,
edit /etc/uptrack/uptrack.conf and
set the https_proxy option (in the [Network] section)
to a value of the form [protocol://]host[:port].
# cat /etc/uptrack/uptrack.conf ... [Network] https_proxy=http://my-proxy.example.com:80/ ... #
Graphical Interface
The graphical interface is currently available for Ubuntu up to Bionic, as part of the free desktop distributions Oracle supports.
After Ksplice Uptrack is installed, a panel icon will notify you when new kernel updates are available:
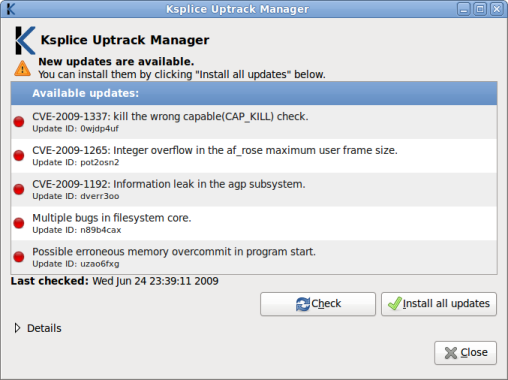
You can click on the icon to view the available updates:
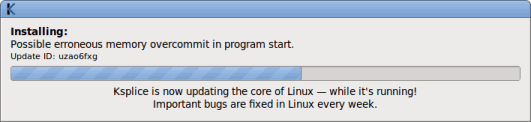
Click the "Install all updates" button to start the update process. A progress bar shows you the updates as they are being installed:
When the process is complete, the update list will look like this:
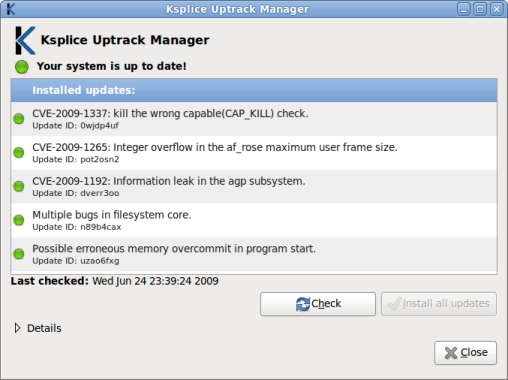
The panel icon will also return to normal:
Your kernel is now up to date and secure!
Access Policies
Each machine under your access key is either allowed or denied access to the Uptrack server. A machine that is denied access will not be allowed to receive updates.
You can set access policies for individual or groups of existing machines as well as set a default access policy for new machines.
Setting Policy for Existing Machines
Using the Web Interface
Individual machines can be allowed or denied access to the Uptrack server from the Allow/Deny Policies pagepage on your web interface. You can also bulk allow or deny machines on that page.
Using the API
Machines can also be allowed or denied via the Uptrack API's
authorize request.
The client library ships with an example script called authorize-uuid
which allows and denies machines using the Python bindings.
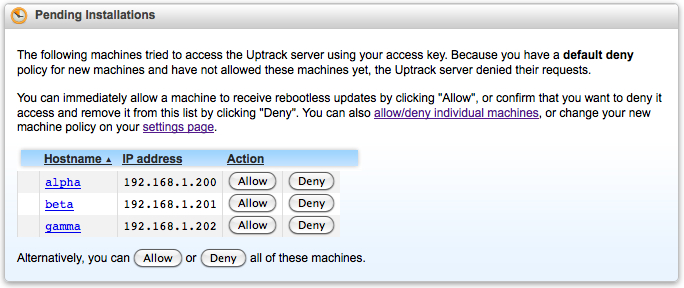
Setting Default Policy for New Machines
The default policy controls how the Ksplice server will respond to requests from machines it has not seen before. The default policy can only be set through the Ksplice system status settings page.
The default policy can be either:
- Allow new machines by default (default allow)
- Under a default allow policy, new machines connecting to the Ksplice Uptrack service using your access key are immediately allowed to receive and install updates from the Uptrack server. Once they connect for the first time they will show up on your web interface as "allowed" unless you change their allow/deny policies.
- Deny new machines by default (default deny)
- Under a default deny policy, new machines are denied access
unless you allow them through the web interface or API.
They are displayed in a special "pending" state on your status interface
for easy monitoring until they have been explicitly allowed or denied: